Interactions and relationships
The section provides the following information:
Understanding the CDM client and our cloud platform
CDM has two main components: a local client and a cloud platform with a web-based admin portal (aka Iris) that allows you to configure and manage CDM.
The CDM client
You can install the CDM client on a standalone Windows computer or a Windows Server in a VDI environment or mass-deploy it across your organization via Group Policy, Command-line Interface, or Microsoft Intune. Once you've installed the CDM client, its icon appears in the system tray, allowing you to interact with it directly from there.
Our cloud platform
The second component, our cloud platform, is hosted in Microsoft Azure. We operate across multiple Microsoft Azure data centers in the UK, EU, and USA. You can choose the region that hosts your data.
Our cloud platform deliberately maintains very little access to your corporate data, as we have no visibility into information stored within your Microsoft environment. This means that even in the worst-case scenario involving comprehensive hacking of our cloud platform, your Microsoft 365 tenancy data would remain protected.
As a service provider, IAM Cloud is a Data Processor; we ingest and process a minimal amount of personal data supplied by you (the Data Controller) to support our services. Our cloud platform does not process or store personal data. However, we may use personal data in the following ways:
-
We validate the legitimacy of each user via their Microsoft 365 UPN/email address. Once processed, this data is immediately deleted and never persisted in our systems or logs.
-
Iris uses both name and email addresses to identify admins. If you don't wish to submit Personally Identifiable Information (PII) as part of your customer setup in Iris, you can use generic identifiers like IT Admin.
By minimizing personal data usage as much as possible, we also aim to control the risk of a data breach: less personal data, less risk of exposure, and less impact of a compromise. Our Data Protection Agreement provides further details on personal data usage and processing.
Finally, access to your service or application-generated data within our cloud platform is limited to a very small number of IAM Cloud support personnel and senior operations staff.
We use an industry-leading support desk system from Freshworks called Freshdesk. Freshdesk is the platform where all our support information is processed and stored. All IAM Cloud accounts in Freshdesk have mandatory multifactor authentication (MFA) enabled. Freshworks also holds ISO 27001 and System and Organization Controls (SOC) certifications.
Our Freshdesk "agents" are provisioned using strict principles of least privilege. These are limited to our technical support team, CTO, COO, and a senior commercial manager. Every member of the team has undergone Baseline Personnel Security Standard (BPSS) vetting as a minimum and undertakes a mandatory monthly security training course. IAM Cloud is also ISO 27001 certified and audited annually as part of this standard.
Our Freshdesk tenancy, policies applying to and processes enacted within Freshdesk, and agents using Freshdesk are all audited and in-scope of our ISO 27001 certification. All the information you submit to us via Freshdesk is stored there for the duration of your contract and an additional 18 weeks. After which, we permanently purge it.
Our cloud platform has three main functions. These include license validation, product configuration retrieval, and Microsoft Graph notification subscription and relay service. License validation and product configuration retrieval are both one-off actions performed when you sign in for the first time to map your drives. The Microsoft Graph notification subscription and relay service is an ongoing process rather than a one-off action, as it alerts CDM about changes to files or folders in Microsoft 365. However, it is essential to note that this does not mean that our cloud platform has access to your data.
Our cloud platform merely subscribes CDM users to the Microsoft Graph notification subscription and relay service and receives the information that this service returns on their behalf as an anonymized remote ID, ensuring that your data is encrypted from the get-go. Upon receipt of this information, our cloud service broadcasts it to the CDM client installed on your desktop. The CDM client then communicates with your Microsoft 365 instance to retrieve the changes and updates the impacted files or folders accordingly. At no point in this process will IAM Cloud or our services have any access to your data.
CDM and Microsoft 365
Microsoft Entra ID permissions used by CDM are 'delegated'. This means that IAM Cloud or our cloud platform can't access your Microsoft 365 tenancy data. CDM is a desktop client, which, with its delegated permissions, can act on behalf of the signed-in user and only do what the signed-in user can do manually. CDM does not grant the user any enhanced privileges, and it cannot act outside of the control or active session of the signed-in user.
CDM provides you with a connection between your Windows desktop/Virtual Desktop Infrastructure (VDI) session and Microsoft 365 account (including OneDrive and SharePoint team sites that you have permission to access) secured by your Microsoft Authentication Library (MSAL) authenticated session. Essentially, CDM is a secure web browser for files. No data can leave the session between your computer and Microsoft 365 account.
CDM interactions
CDM has two core interactions—one with our cloud platform and the other with Microsoft 365.
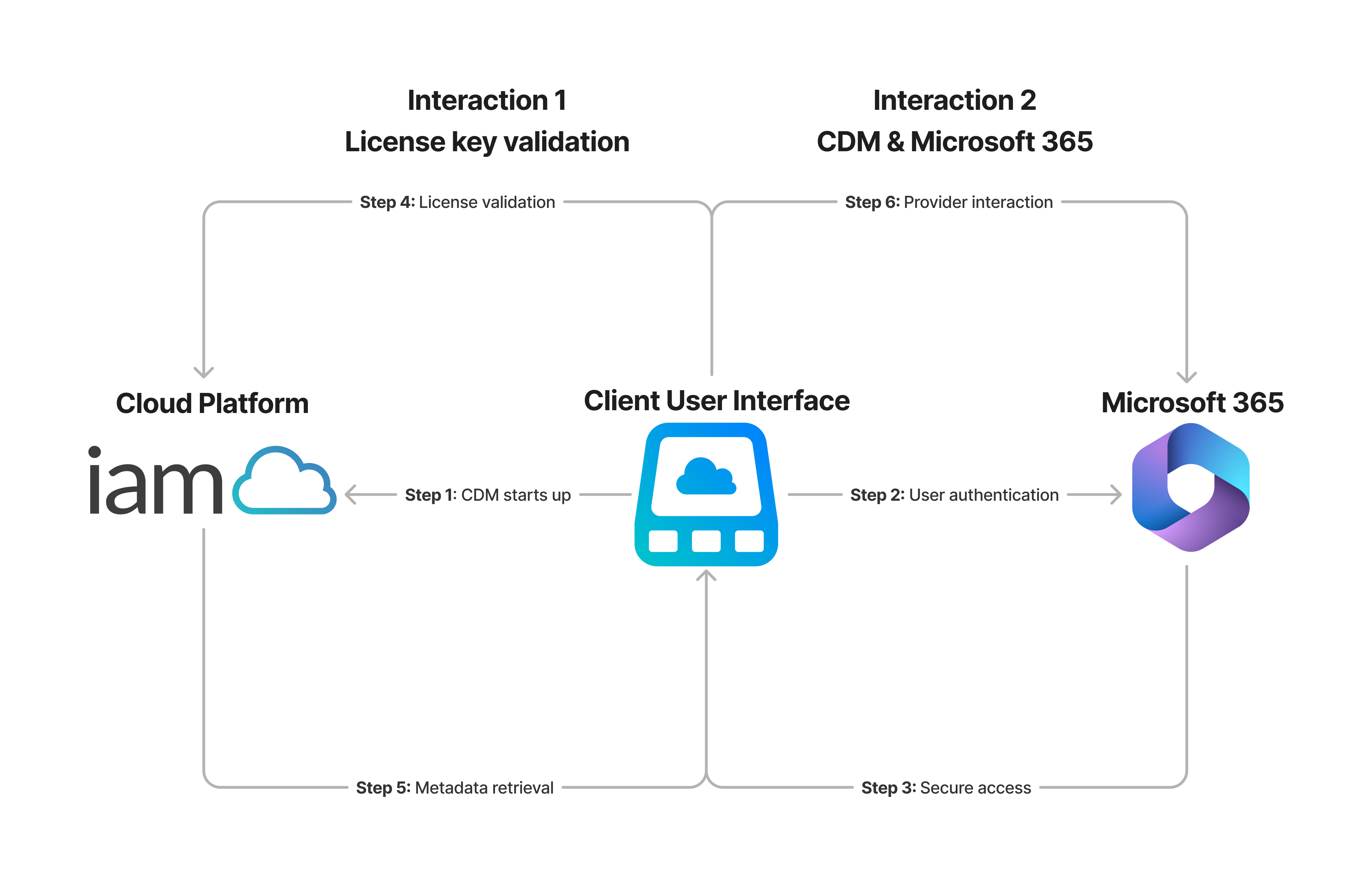
-
Step 1 As soon as CDM starts up, it calls Bifrost (the IAM Cloud API hosted on our cloud platform) to retrieve its initial instructions in the form of a startup policy.
-
Step 2 To integrate with your Microsoft 365 tenant, CDM needs access to Microsoft APIs such as Microsoft Graph and SharePoint REST APIs. To do so, CDM retrieves the local user's User Principal Name (UPN) and, via the MSAL framework, attempts to authenticate to Microsoft 365 on your behalf.
-
Step 3 On successful authentication, Microsoft 365 provides an authorized access token to CDM. This process fully complies with SSO, MFA, and conditional access as CDM adheres to the security settings configured for your Microsoft 365 tenant. Permissions configured in Microsoft Entra ID govern the relationship between CDM and Microsoft APIs.
-
Step 4 Once you're signed in, CDM retrieves your license key from the Registry (HKCU or HKLM registry hives) and calls Bifrost again to confirm the validity of your license.
-
Step 5 Bifrost responds by returning metadata about drives, mapping groups, and policy configurations associated with your license key.
-
Step 6 CDM uses the metadata from Bifrost (the IAM Cloud API) to determine what drives to map. The communication between CDM and your Microsoft 365 account is protected using a Transport Layer Security (TLS) 1.2 or higher-encrypted HTTPS connection.






